How and why?
Deep Web vs. Dark Web: How They Work and Why They Matter
The internet is a vast, multi-layered space, with much of its content hidden from everyday users. Beneath the familiar websites lies a world few truly understand the Deep Web and its shadowy counterpart, the Dark Web. These hidden realms are shrouded in mystery and often misunderstood, yet they play pivotal roles in our digital age. Dive into this exploration to uncover how these hidden layers function and why they are crucial in today’s interconnected world.
Introduction
Have you ever wondered what lies beneath the surface of the internet? Beyond the easily accessible websites you visit daily, vast amounts of data remain hidden from public view. This unseen portion of the internet, known as the Deep Web, and its more clandestine subset, the Dark Web, hold the key to understanding online privacy, security, and even illegal activities. Join us as we unravel these enigmatic layers and discover their significance in the digital landscape.
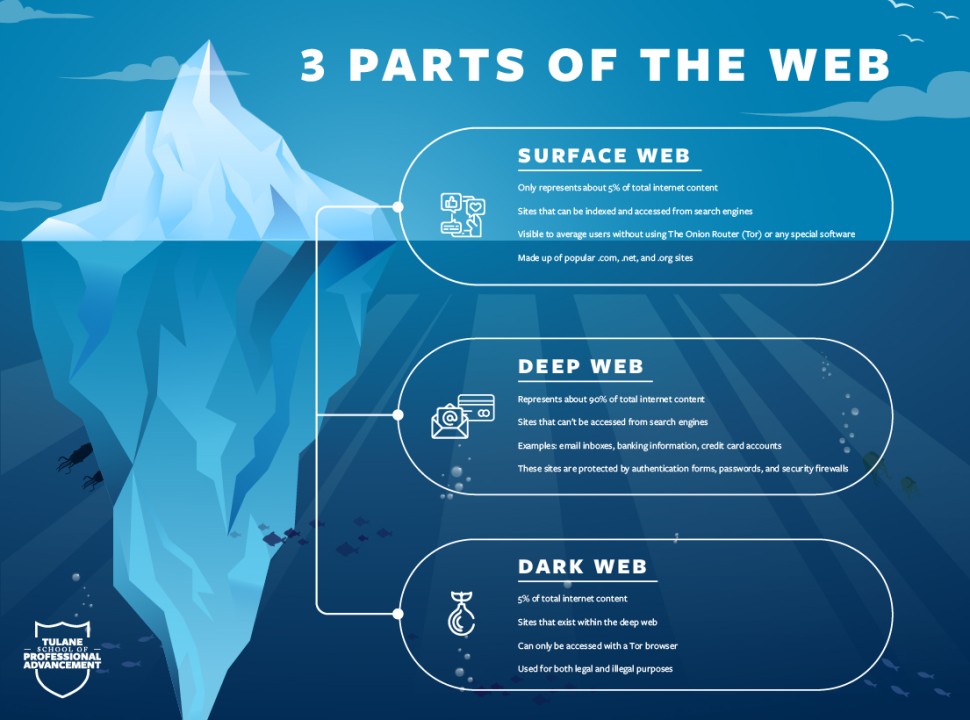
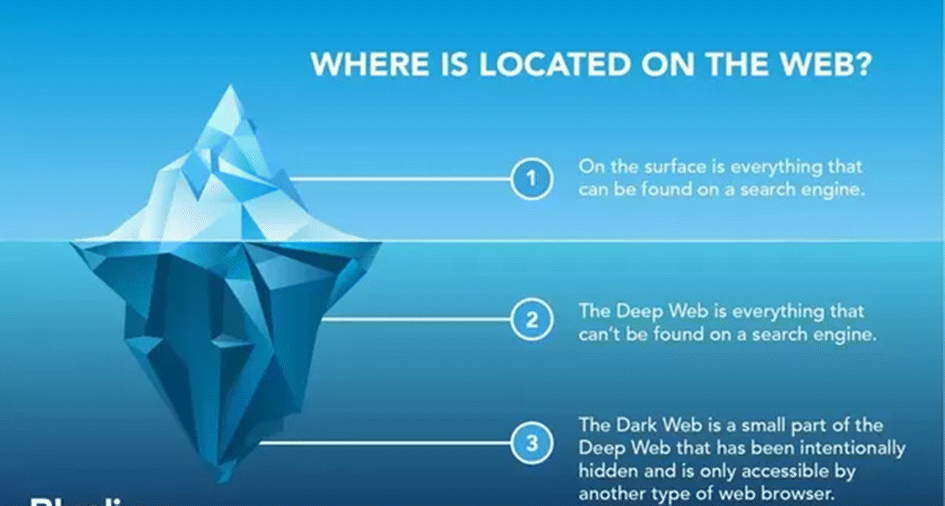
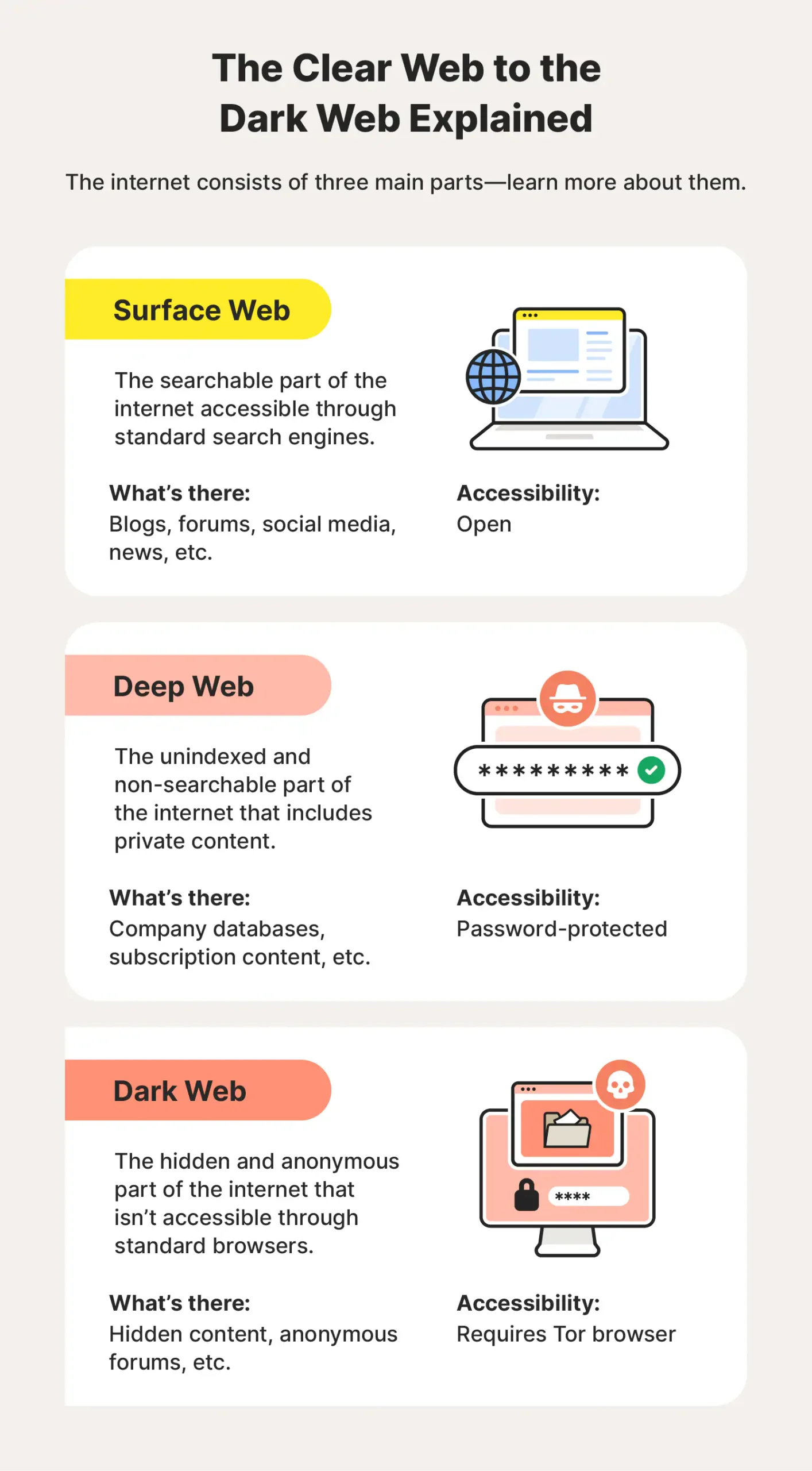
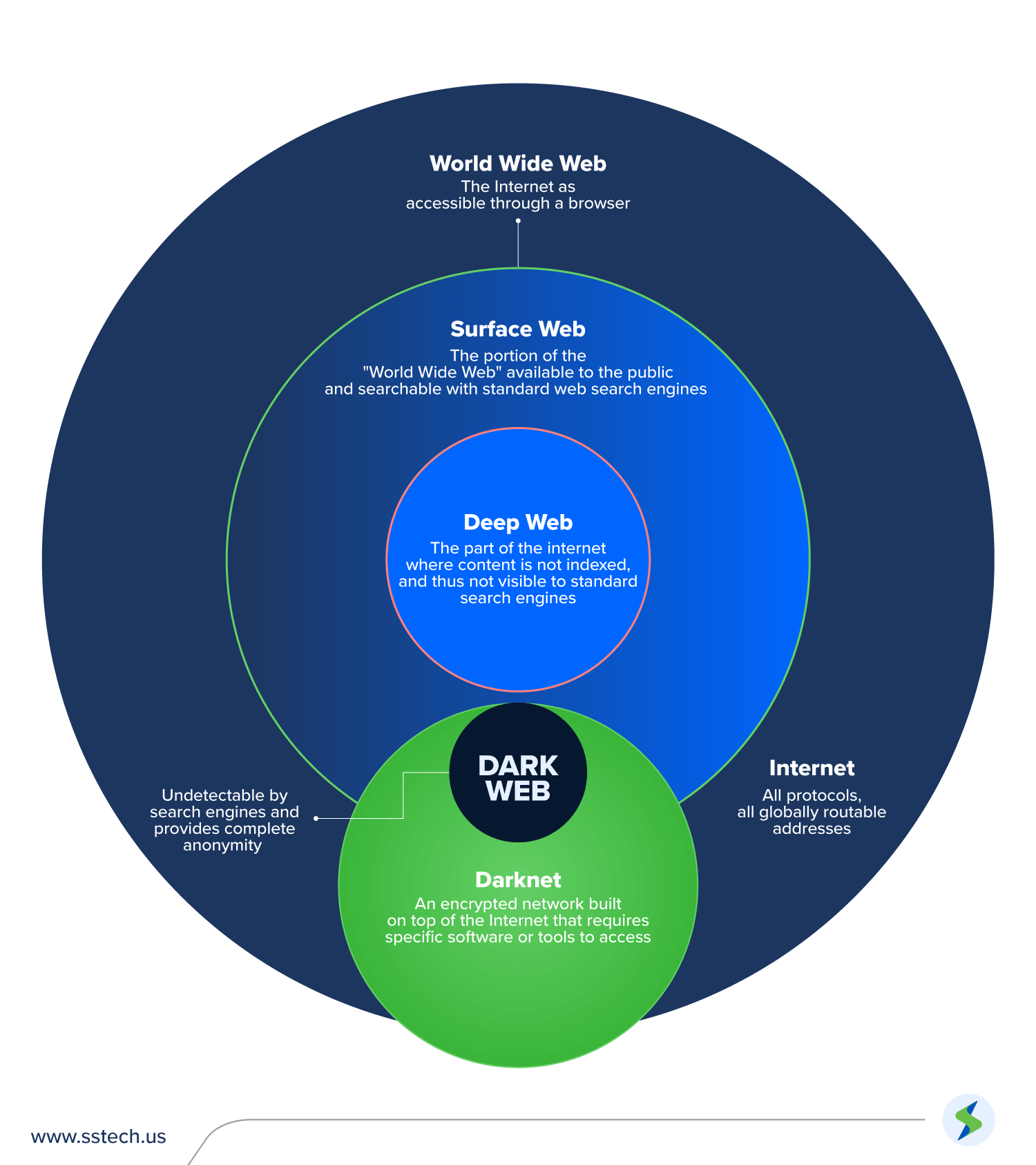
What are the Deep Web and Dark Web?
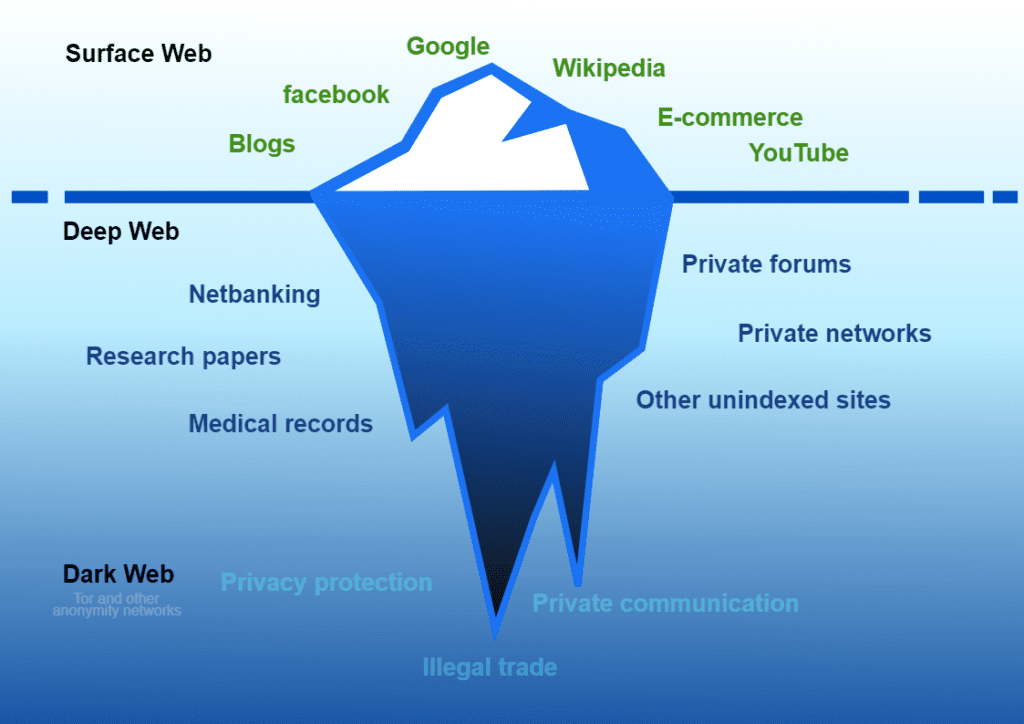
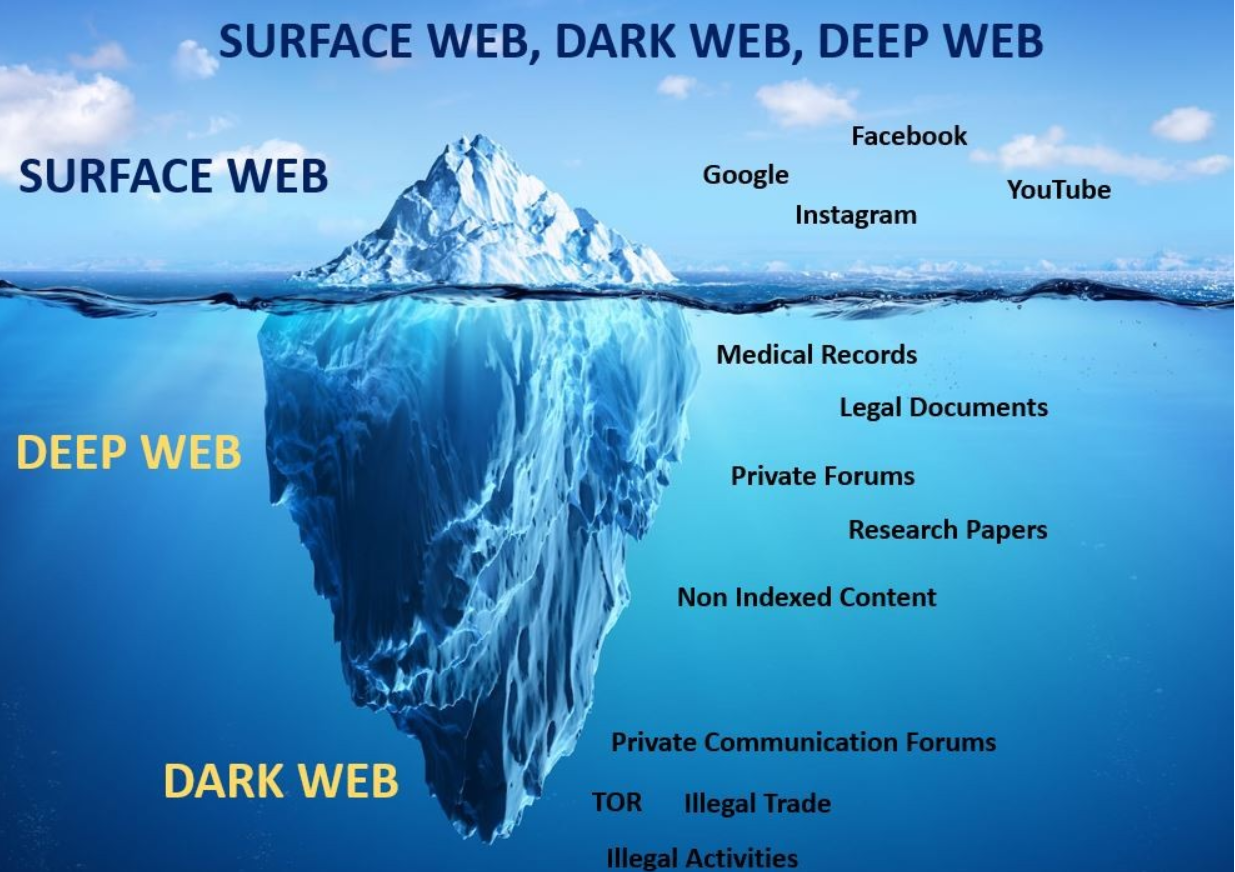
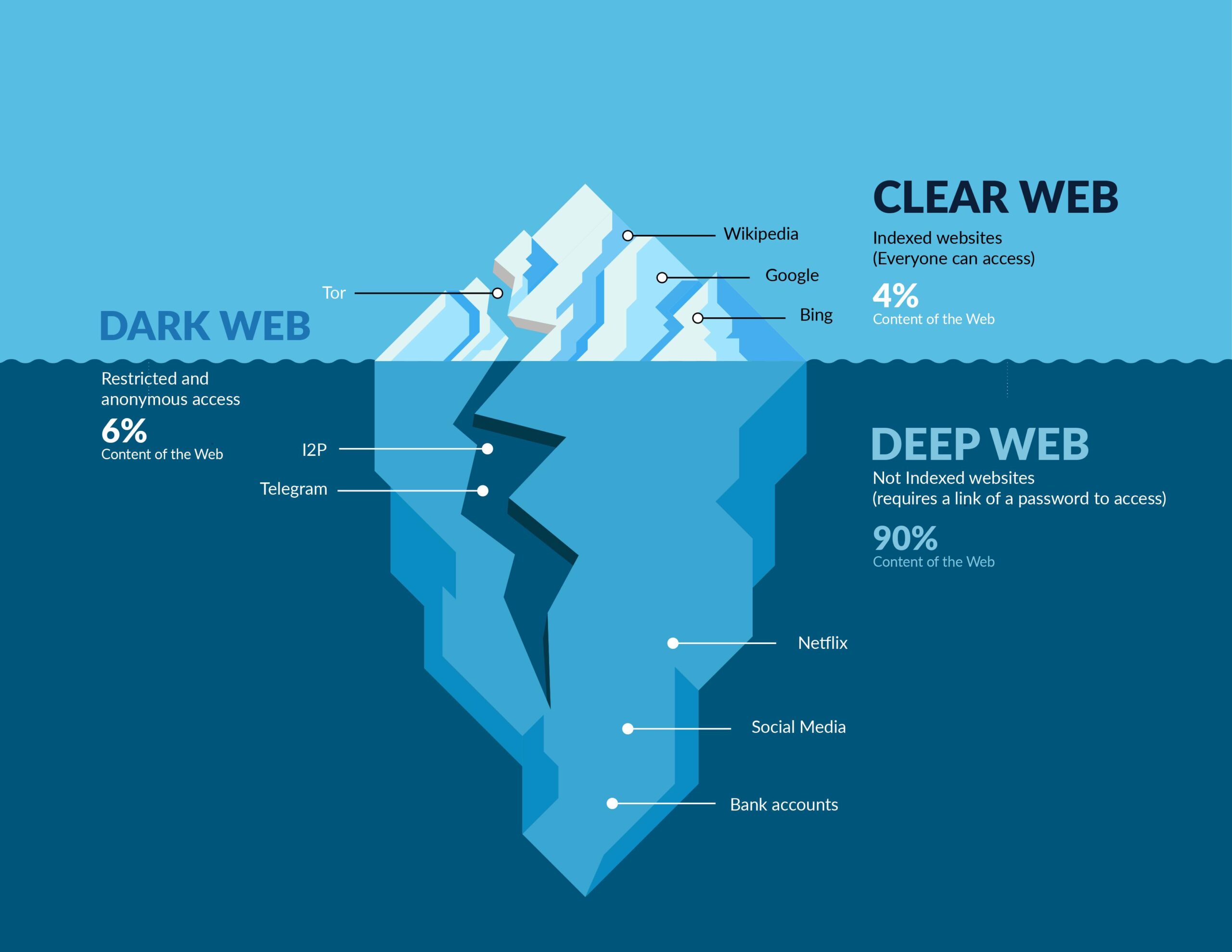
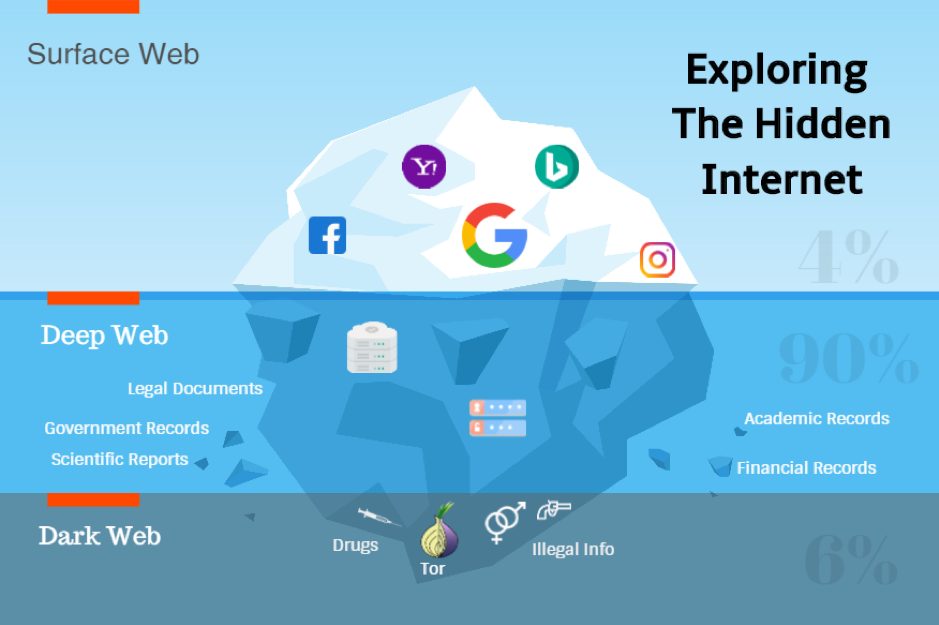
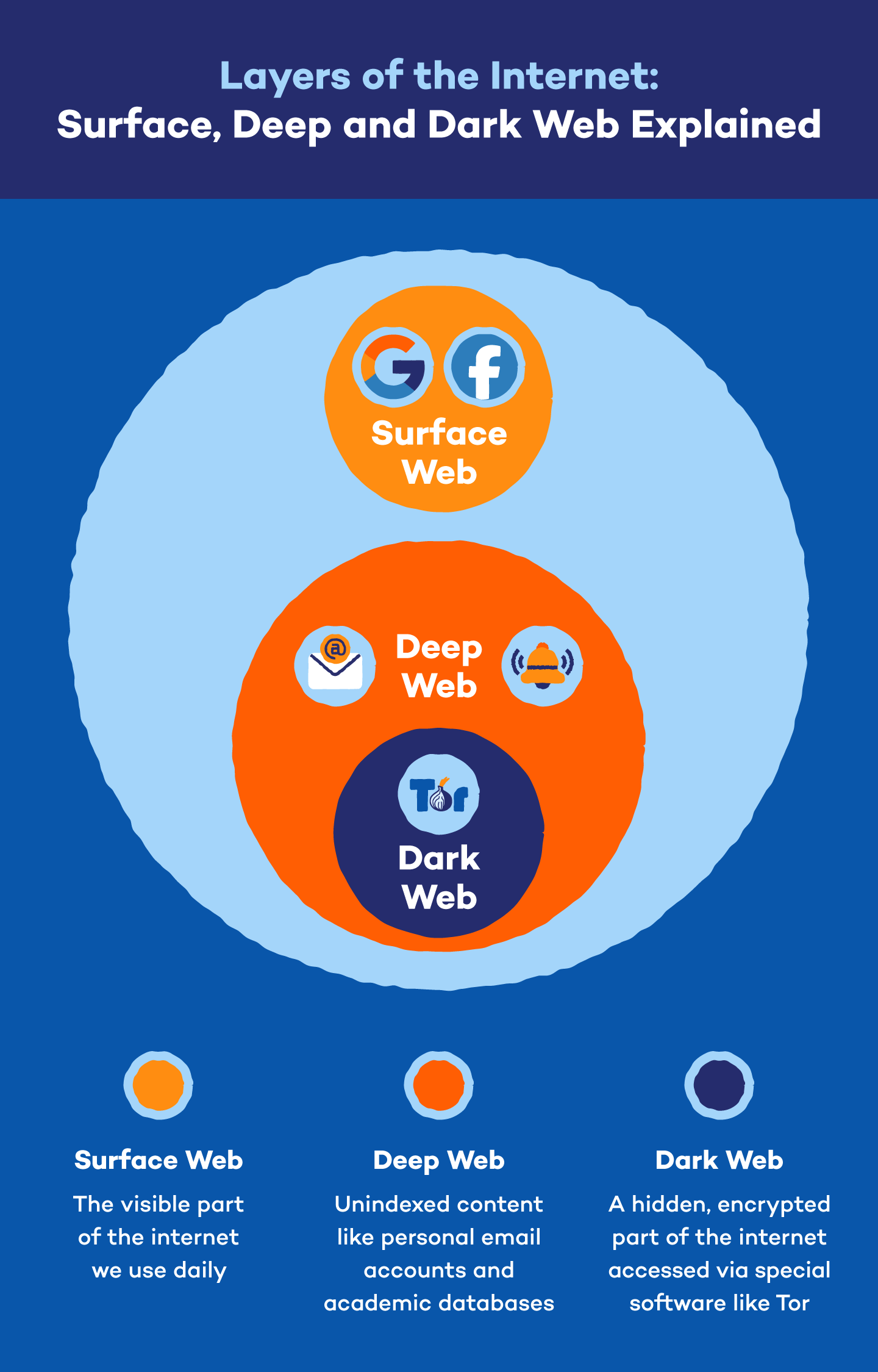
The internet is often visualized as a vast pyramid, with the surface web as the visible top layer easily accessible via standard search engines like Google or Bing. However, this only represents a small fraction around 4-10% of all online content. The Deep Web constitutes the majority, encompassing approximately 90-95% of the internet. This layer includes various forms of data that are not indexed by search engines, such as private databases, academic resources, financial records, and personal information.
Key Components of the Deep Web:
- Academic Databases: Repositories like JSTOR and PubMed contain scholarly articles and research papers accessible only to subscribers or affiliated institutions.
- Subscription Services: Platforms like Netflix or academic journals require user authentication, keeping their content hidden from public search indexes.
- Personal Accounts: Online banking, email services, and social media accounts store sensitive information that remains secure behind login credentials.
In contrast, the Dark Web is a specific segment of the Deep Web deliberately concealed and inaccessible without specialized tools. It requires software like the Tor browser, which anonymizes user activity by routing traffic through a network of servers, ensuring privacy and security. This anonymity fosters both positive and negative uses from protecting activists in oppressive regimes to enabling illegal marketplaces for drugs, weapons, and stolen data.
| Feature | Deep Web | Dark Web |
|---|---|---|
| Accessibility | Requires authentication for access | Requires specialized software (e.g., Tor) |
| Content Type | Academic resources, personal data | Illegal marketplaces, anonymous forums |
| Purpose | Protect sensitive information | Ensure user anonymity and privacy |
| Indexing | Not indexed by standard search engines | Not indexed; hidden intentionally |
Understanding these distinctions is crucial for navigating the complexities of the internet, as each layer serves distinct purposes and presents unique challenges and opportunities.

Why People Confuse the Deep Web with the Dark Web
Misconceptions about the Deep Web and Dark Web often stem from a lack of clear terminology and understanding. Both terms refer to sections of the internet not indexed by standard search engines, leading many to believe they are interchangeable. However, the differences between the two are significant and have important implications for privacy, security, and legality.
Common Reasons for Confusion:
- Similar Terminology: Both terms include “web,” leading to the assumption they are the same.
- Hidden Nature: The fact that both are not accessible via conventional search engines fosters confusion.
- Media Representation: News and media often conflate the two, emphasizing the Dark Web’s illicit aspects, which overshadow the broader, legitimate uses of the Deep Web.
- Association with Illicit Activities: The Dark Web’s association with illegal activities overshadows the legitimate uses of the Deep Web, creating a skewed perception.
Example Comparison:
| Aspect | Deep Web | Dark Web |
|---|---|---|
| Scope | Encompasses most of the internet | A small portion of the Deep Web |
| Usage | Academic research, private communications | Illicit trade, anonymous communication |
| Accessibility | Requires credentials | Requires specialized tools like Tor |
| Perception | Generally neutral | Often associated with criminal activities |
This confusion highlights the importance of educating users about the distinct functionalities and purposes of each layer to foster a more accurate understanding of the internet’s structure.
Why It’s Important to Understand Their Differences
Grasping the differences between the Deep Web and Dark Web is essential for several reasons. It not only demystifies the workings of the internet but also equips users with the knowledge to navigate these spaces safely and responsibly.
Significance of Understanding Differences:
- Enhanced Cybersecurity: Knowing which parts of the web store sensitive information helps in implementing appropriate security measures.
- Informed Privacy Choices: Users can make better decisions regarding their online privacy and the platforms they engage with.
- Legal Awareness: Understanding what constitutes illegal activity on the Dark Web versus legitimate uses of the Deep Web helps in avoiding unintentional legal infractions.
- Educational and Professional Use: Researchers and professionals can access the necessary resources within the Deep Web for their work without compromising security.
Moreover, recognizing these differences aids in combating misconceptions that can lead to fear or misuse of these internet layers. By distinguishing between the vast, mostly benign Deep Web and the smaller, more volatile Dark Web, individuals can better appreciate the internet’s complexity and the importance of maintaining both accessibility and security.
Implications for Society:
- Privacy Protection: Ensures that personal data is safeguarded in the Deep Web.
- Law Enforcement: Helps authorities target illicit activities on the Dark Web without hindering legitimate uses.
- Technological Development: Encourages the creation of tools and policies that balance openness and privacy.
In summary, understanding the distinctions between the Deep Web and Dark Web is crucial for harnessing the internet’s full potential while mitigating associated risks.
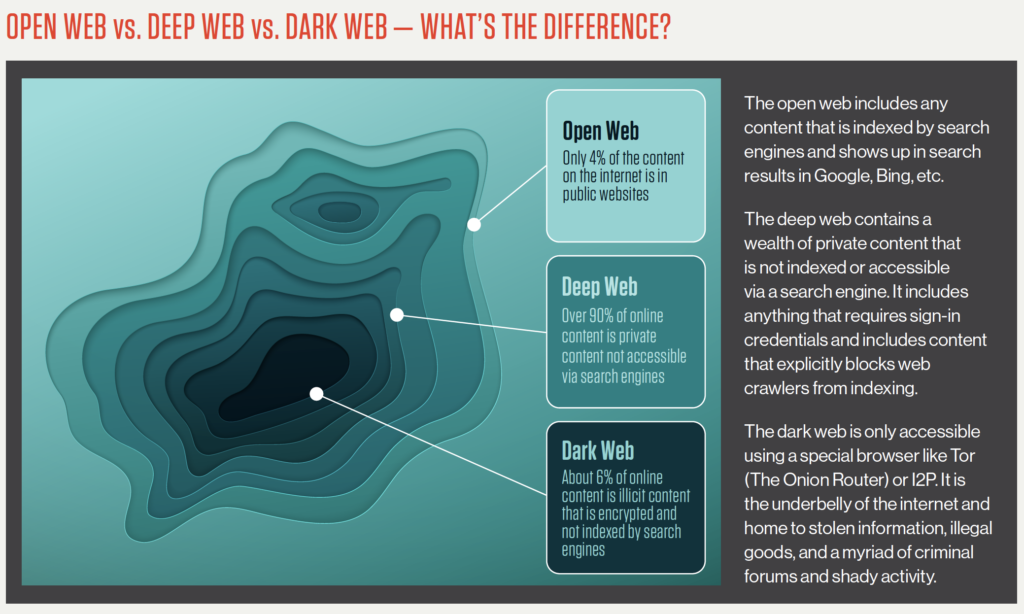
How the Deep Web Works
The Deep Web operates behind various security measures, ensuring that vast amounts of information remain inaccessible to unauthorized users. Understanding its mechanics is fundamental to appreciating its role in the internet ecosystem and its importance for privacy and security.
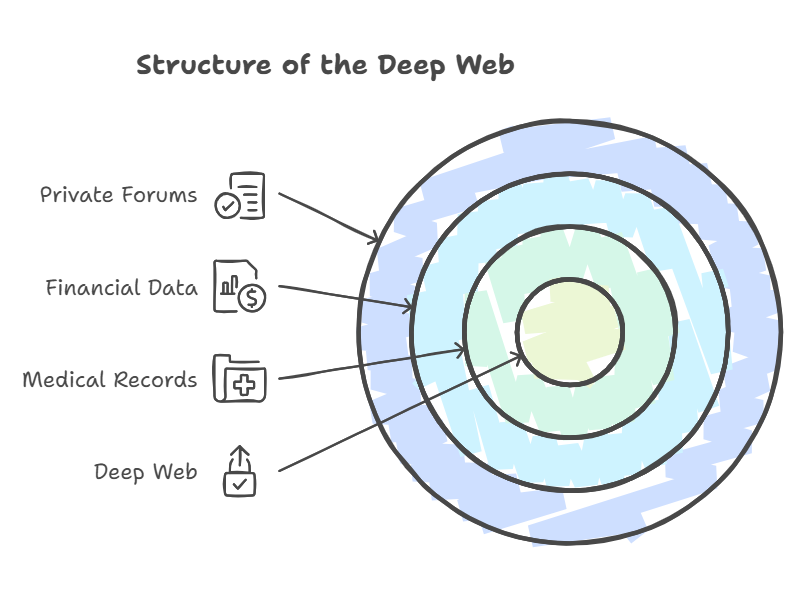
How the Deep Web is Structured
The Deep Web’s structure is hierarchical and complex, designed to cater to a myriad of secure information storage and access needs. This structure ensures that while certain data is available to those with the right permissions, it remains hidden from general search engine indexing.
Key Structural Elements:
- Private Databases: These include academic libraries, corporate records, and government databases that require specific access credentials.
- Intranets: Corporate or institutional intranets serve as internal communication and data storage platforms, isolated from the public internet.
- Dynamic Content: Websites that generate content dynamically based on user input or specific queries (e.g., search results tailored to individual requests) are part of the Deep Web because their content cannot be easily crawled by search engines.
Example of Deep Web Structure:
| Layer | Description | Examples |
|---|---|---|
| Base Layer | Public, indexed content easily accessible via search engines | Main websites, blogs, news portals |
| Middle Layer | Authenticated, secure content requiring credentials | Online banking, email services |
| Core Layer | Highly secure, often isolated databases and internal systems | Government databases, corporate intranets |
This multi-tiered structure ensures that sensitive information is protected while still being accessible to authorized users, providing a balance between accessibility and security.
How Users Access the Deep Web
Accessing the Deep Web is generally straightforward for those with the right credentials and knowledge. Unlike the Dark Web, it does not require specialized software, but rather, relies on secure authentication methods.
Steps to Access the Deep Web:
- Authentication: Users must log in using secure credentials such as usernames and passwords. This ensures that only authorized individuals can access the protected content.
- Secure Connections: Encrypted protocols like HTTPS are commonly used to protect data during transmission.
- Access Control: Multi-factor authentication (MFA) may be employed to add an extra layer of security, requiring additional verification beyond just a password.
Access Methods:
- Subscription Services: Platforms like Netflix or academic journals require users to subscribe, granting access to their content.
- Institutional Access: Universities and research institutions provide their members with access to proprietary databases and resources.
- Private Networks: Organizations use VPNs and other secure networks to allow remote access to their internal systems.
By leveraging these secure access methods, the Deep Web ensures that sensitive information remains protected while still accessible to those who need it.
How Websites and Databases Stay Hidden from Search Engines
Websites and databases within the Deep Web employ various strategies to prevent indexing by search engines, ensuring that their content remains hidden from the general public.
Techniques to Stay Hidden:
- Robots.txt Files: Directives in robots.txt files can instruct search engines not to crawl certain pages or directories.
- Meta Tags: Using meta tags like “noindex” can prevent individual pages from being indexed even if they are accessible via a search engine.
- Dynamic URLs: Pages that generate unique URLs based on user queries or inputs are not easily indexed by crawlers.
- Authentication Requirements: Requiring logins ensures that content remains inaccessible to search engine bots, which cannot log in to access the information.
Table of Techniques:
| Technique | Description | Purpose |
|---|---|---|
| Robots.txt | File containing rules for search engine crawlers | Prevents crawling of specified directories or pages |
| Meta Tags | HTML tags that can instruct search engines not to index a page | Ensures specific content stays unindexed |
| Dynamic URLs | URLs that change based on user interactions | Makes pages non-static and harder for crawlers to index |
| Authentication | Requiring user login for access | Restricts access to authorized users only |
These techniques collectively ensure that sensitive or proprietary content remains concealed from public search engines, thereby maintaining the confidentiality and security of the information housed within the Deep Web.
Why the Deep Web Exists
The Deep Web serves crucial functions that cater to privacy, security, and the efficient management of vast amounts of data, making it an indispensable part of the internet infrastructure.

Why Some Information Needs to Be Hidden from Public Search
Certain types of information are sensitive or proprietary and must remain confidential to protect privacy, security, or competitive advantage. The reasons for hiding information from public search engines are varied and essential for maintaining the integrity and safety of individuals and organizations.
Reasons for Concealing Information:
- Privacy Concerns: Protecting personal data from unauthorized access helps prevent identity theft and privacy breaches.
- Security Requirements: Sensitive information such as governmental or military data must be shielded to prevent misuse or threats to national security.
- Competitive Advantage: Businesses safeguard proprietary information, trade secrets, and internal communications to maintain their competitive edge.
- Legal Compliance: Regulations like HIPAA for health information or GDPR for data protection mandate that certain data remain confidential and secure.
- Intellectual Property Protection: Research and development outputs are often kept confidential to safeguard intellectual property before it is publicly disclosed.
List of Information Categories:
- Medical Records: Protected under regulations like HIPAA to ensure patient confidentiality.
- Financial Data: Online banking information and transaction records require robust security measures.
- Corporate Data: Internal communications, strategic plans, and proprietary technology are kept hidden to prevent competitive disadvantage.
- Personal Identifiable Information (PII): Includes social security numbers, addresses, and other personal details that need protection from unauthorized access.
These factors underscore the necessity of keeping certain information hidden from public searches to ensure privacy, security, and operational integrity.
Why Online Banking, Email, and Private Data Are Part of the Deep Web
Online banking platforms, email services, and other private data repositories are quintessential components of the Deep Web, playing a pivotal role in daily digital activities while ensuring security and privacy.
Key Aspects How These Services Are Protected:
- User Authentication: Banks and email providers require secure logins, often with multi-factor authentication, to verify user identities.
- Data Encryption: Sensitive data is encrypted both in transit and at rest to prevent unauthorized access.
- Access Control: Strict access policies ensure that only authorized personnel can view or modify sensitive information.
- Compliance with Regulations: Services must adhere to data protection laws and industry standards to maintain the confidentiality and integrity of user data.
Reasons These Services Are Deep Web Components:
- Security: Protecting financial transactions and personal communications from cyber threats.
- Privacy: Ensuring user data remains confidential and is not accessible to unauthorized parties.
- Reliability: Maintaining high uptime and secure access for critical online services.
- Efficiency: Allowing seamless access to personal data across secure networks without exposing them to public search engines.
Table of Common Deep Web Services:
| Service | Description | Security Measures |
|---|---|---|
| Online Banking | Platforms for managing financial transactions and accounts | MFA, encryption, secure logins |
| Email Services | Secure communication tools with private messaging | Encryption, spam filters, secure storage |
| Private Data Repositories | Databases storing personal and corporate information | Access controls, data encryption |
By integrating robust security protocols, these services ensure that user data remains protected while facilitating essential online activities, underscoring the Deep Web’s role in safeguarding sensitive information.
Why the Deep Web is Essential for Cybersecurity and Privacy
The Deep Web is a cornerstone for maintaining cybersecurity and privacy across the digital landscape. Its intricate structure and protective measures provide a secure environment for handling sensitive data, thus playing a critical role in safeguarding personal and organizational information.
Importance of the Deep Web in Cybersecurity:
- Data Protection: By keeping sensitive information hidden, the Deep Web minimizes the risk of data breaches and cyber attacks.
- Secure Communication: Organizations can communicate internally without exposing their data to potential cyber threats.
- Regulatory Compliance: The Deep Web helps businesses comply with data protection regulations by securely storing and managing sensitive information.
- Risk Mitigation: Protecting critical infrastructure data from public view reduces vulnerabilities that could be exploited by malicious actors.
Key Roles in Privacy:
- Anonymity: Ensures that users can safely conduct their online activities without exposing personal details.
- Data Integrity: Maintains the accuracy and reliability of data by preventing unauthorized access and modifications.
- Access Control: Restricts data access to authorized individuals, enhancing overall data security.
Examples of Deep Web’s Role in Cybersecurity:
- Companies use internal databases to store proprietary information, ensuring that intellectual property remains secure.
- Healthcare Providers maintain patient records in secured databases to protect sensitive health information from unauthorized access.
- Financial Institutions safeguard customer data and transaction histories, preventing fraud and ensuring the integrity of financial operations.
By providing a secure infrastructure for storing and managing sensitive data, the Deep Web is indispensable for both cybersecurity and privacy, enabling safe and efficient digital operations in an age where data is a valuable asset.
How the Dark Web Works
Building upon the foundation of the Deep Web, the Dark Web introduces a layer of anonymity and privacy that fundamentally alters how information is accessed and shared. Understanding its operation is key to grasping its dual nature and the associated risks and benefits.
How the Dark Web Differs from the Deep Web
While the Deep Web pertains to all unindexed parts of the internet, the Dark Web is a deliberate subset within it, distinguished by its strong emphasis on anonymity and privacy. These distinctions set the Dark Web apart in terms of accessibility, content, and purpose.
Key Differences:
- Accessibility: The Dark Web requires specialized software like Tor to access, whereas the Deep Web can be accessed using conventional browsers with the right credentials.
- Content Nature: The Dark Web often hosts illicit content such as illegal marketplaces, hacking forums, and stolen data, in contrast to the Deep Web’s legitimate uses like secure databases and personal accounts.
- Anonymity Level: Users on the Dark Web remain highly anonymous, facilitating both privacy-focused activities and illegal operations.
Comparison Table:
| Feature | Deep Web | Dark Web |
|---|---|---|
| Accessibility | Requires login credentials | Requires specialized tools like Tor |
| Content Type | Secure databases, personal accounts | Illicit marketplaces, anonymous forums |
| Purpose | Protect sensitive information | Ensure user anonymity and privacy |
| Security Measures | Encryption, authentication | Onion routing, encryption |
- Usage Groups: The Dark Web attracts not only criminals but also activists, whistleblowers, and journalists seeking to communicate securely without fear of surveillance.
Understanding these differences is vital to comprehending how each segment of the unindexed internet serves distinct functions, supporting both legitimate privacy needs and facilitating illegal activities.
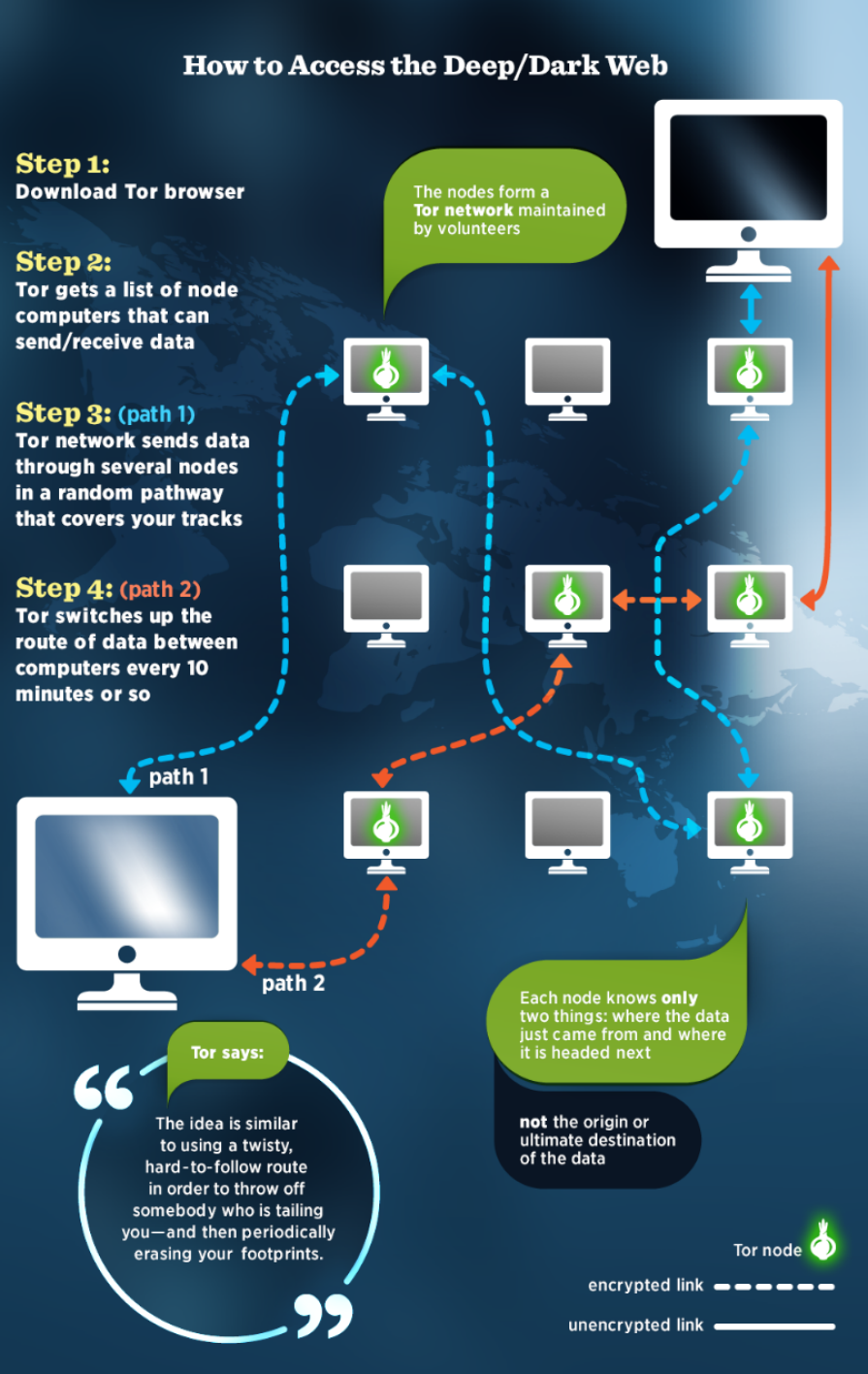
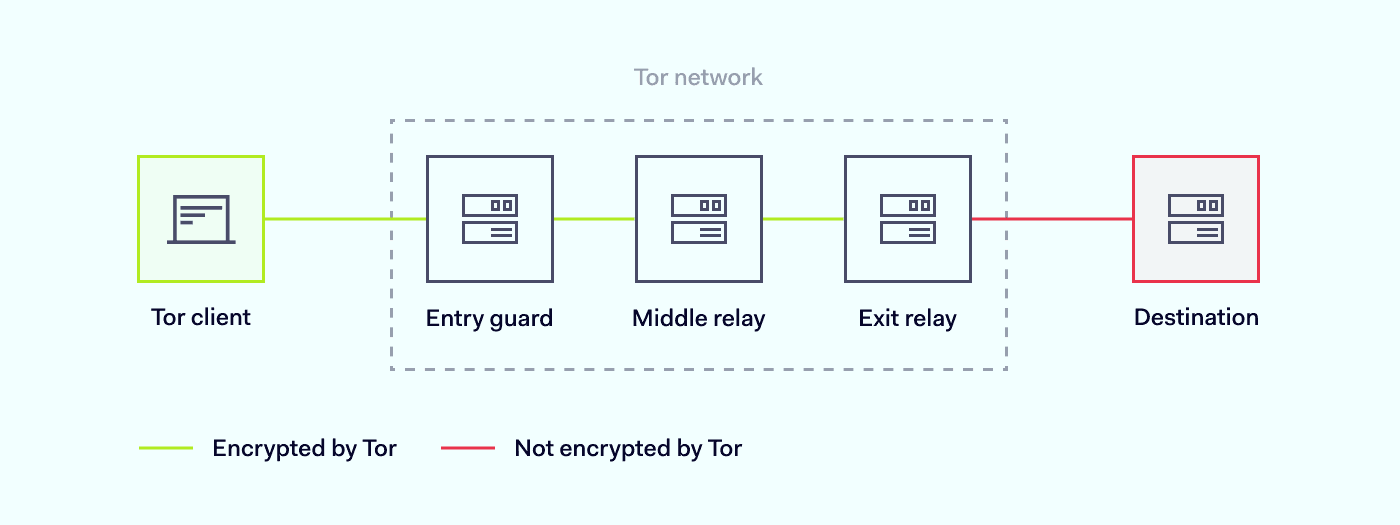
How Tor and Other Anonymity Networks Enable Access
Access to the Dark Web is facilitated primarily through anonymity networks like Tor, which provide the necessary tools for maintaining user privacy and securing communications.
Mechanism of Tor:
- Onion Routing: Tor encrypts data in layers, similar to an onion, routing it through multiple volunteer-operated servers (nodes).
- Random Path Selection: Each data packet takes a random path through several nodes, making it difficult to trace the origin of the traffic.
- .onion Domains: Websites on the Dark Web utilize .onion domains, accessible only via Tor, adding an extra layer of anonymity.
How Tor Works:
- Data Encryption: Data sent through Tor is encrypted multiple times, ensuring that no single node can decipher complete information.
- Relay System: Data traverses through at least three nodes entry, relay, and exit each only knowing the immediate predecessor and successor, not the entire path.
- Anonymity Preservation: By separating the user’s IP address from their online activity, Tor protects user identities from being tracked.
Other Anonymity Networks:
- I2P (Invisible Internet Project): A decentralized network designed for secure and anonymous communication, often used for various forms of private hosting and forums.
- Freenet: Focused on censorship-resistant communication, Freenet allows users to publish information without fear of it being removed or traced back.
| Network | Primary Function | Unique Feature |
|---|---|---|
| Tor | Anonymizing internet traffic | Onion routing and .onion domains |
| I2P | Secure, anonymous peer-to-peer communication | Internal network for anonymous apps |
| Freenet | Censorship-resistant publishing | Decentralized data storage |
These networks are crucial for accessing the Dark Web, offering the anonymity and security that make the Dark Web both a haven for privacy-focused individuals and a breeding ground for covert and sometimes illegal activities.
How Transactions and Communication Are Kept Private
The Dark Web employs robust technologies to ensure that transactions and communication remain private and secure, fostering an environment where anonymity is preserved.
Privacy Mechanisms:
- Encryption: End-to-end encryption protects messages and transactions from being intercepted and read by unauthorized parties.
- Cryptocurrencies: Digital currencies like Bitcoin and Monero are widely used for transactions, providing a layer of financial anonymity.
- Secure Messaging Apps: Platforms such as Signal and encrypted email services allow users to communicate without revealing their identities.
Key Elements of Private Transactions:
- Cryptocurrency: Bitcoin is popular due to its decentralized nature, while Monero offers enhanced anonymity features, making transactions harder to trace.
- Escrow Services: Many Dark Web marketplaces use escrow services to secure payments, ensuring that transactions are only completed when both parties are satisfied.
- Anonymity Tools: Tools like mixers (or tumblers) are used to further anonymize cryptocurrency transactions by blending multiple transactions into one.
Privacy in Communication:
- Tor Browser: Ensures that browsing activities cannot be easily monitored or traced.
- Encrypted Emails and Messages: Use of secure protocols like PGP (Pretty Good Privacy) for email encryption ensures that only the intended recipient can read the message content.
- Onion Services: These services communicate exclusively within the Tor network, adding an additional layer of security.
By integrating these technologies, the Dark Web ensures that users can transact and communicate with a high degree of anonymity and security, protecting their identities and sensitive information from potential threats.
Why the Dark Web Exists
The Dark Web serves as a refuge for anonymity and privacy, catering to a diverse range of users with varying needs, from legitimate concerns to illicit activities. Its existence is driven by the need to protect individual freedoms and secure sensitive information in a world increasingly monitored by surveillance technologies.
Why Some People Use the Dark Web for Privacy Protection
Individuals seek the Dark Web to maintain privacy and anonymity in their online activities, especially in environments where surveillance and censorship are prevalent. This need for privacy is driven by various personal and professional motivations.
Privacy Protection Reasons:
- Avoiding Surveillance: Users concerned about government surveillance, corporate tracking, or data harvesting use the Dark Web to keep their activities private.
- Protecting Personal Identity: Individuals vulnerable to stalking, harassment, or identity theft find anonymity crucial for their safety.
- Freedom of Expression: Activists and whistleblowers can speak freely without fear of retaliation or censorship when using the Dark Web.
- Bypassing Censorship: In countries with strict internet censorship, the Dark Web provides access to unrestricted information and communication channels.
Use Cases:
- Whistleblowing: Platforms like SecureDrop allow whistleblowers to anonymously share sensitive information with journalists.
- Activism: Activists use the Dark Web to organize, communicate, and share information without drawing attention from oppressive regimes.
- Private Communication: Individuals desiring secure communication channels for personal or professional reasons utilize Dark Web tools to protect their conversations.
Comparison with the Surface Web:
- Anonymity: Surface Web users are easily traceable, whereas Dark Web users enjoy high levels of anonymity.
- Security Measures: Enhanced encryption and anonymizing tools on the Dark Web provide greater security for sensitive communications.
- Access Restrictions: The Dark Web requires specific tools and knowledge, making it less accessible but more secure for privacy-centric use.
Understanding why individuals choose the Dark Web underscores its importance as a tool for privacy protection, enabling secure communication and safeguarding personal freedoms in an era of growing digital surveillance.

Why Governments and Journalists Use the Dark Web for Secure Communication
Governments and journalists leverage the Dark Web to facilitate secure and confidential communication, ensuring that sensitive information remains protected from interception and censorship.
Government Use Cases:
- Intelligence Communication: Agencies use secure Dark Web channels to communicate sensitive intelligence without exposing sources.
- Secure Operations: Planning and coordinating covert operations can be conducted more securely through Dark Web communications.
Journalist Use Cases:
- Source Protection: Journalists use encrypted communication to protect the identities of their sources, particularly in high-risk environments.
- Secure Correspondence: SecureDrop and similar platforms allow journalists to receive confidential tips and documents without compromising source anonymity.
- Investigative Journalism: Access to hidden information and networks on the Dark Web aids in uncovering corruption, illicit activities, and other critical investigative topics.
Benefits:
- Enhanced Security: Communication remains secure and resistant to external monitoring or hacking attempts.
- Anonymity: Protects both the government officials and journalists from being traced, ensuring their safety and the integrity of their work.
- Reliability: Provides a consistent and secure method for exchanging sensitive information under restrictive conditions or in hostile environments.
Comparison with Traditional Communication Channels:
| Feature | Traditional Channels | Dark Web Channels |
|---|---|---|
| Anonymity | Limited | High |
| Security | Moderate, susceptible to breaches | High, with robust encryption and anonymization |
| Accessibility | Easily accessible | Requires specialized software like Tor |
| Censorship Resistance | Vulnerable to blocking | Resistant to censorship and surveillance |
By utilizing the Dark Web, governments and journalists ensure that their critical communications remain secure, anonymous, and resistant to external threats, making it an invaluable tool for maintaining confidentiality and integrity in sensitive operations.
Why the Dark Web Attracts Illegal Activities
The Dark Web’s inherent anonymity and lack of regulation make it a fertile ground for various illegal activities, attracting individuals and groups seeking to operate beyond the reach of law enforcement and conventional oversight.
Factors Attracting Illicit Use:
- Anonymity: Users can operate without fear of being identified, making it ideal for conducting illegal transactions anonymously.
- Lack of Regulation: The Dark Web lacks the same regulatory frameworks as the surface web, providing fewer restrictions on what can be hosted and traded.
- Cryptocurrency Payments: The use of cryptocurrencies like Bitcoin and Monero facilitates anonymous transactions, making it easier to buy and sell illicit goods without a trace.
Types of Illegal Activities:
- Drug Trafficking: Marketplaces like Silk Road (now defunct) enabled the anonymous sale of narcotics.
- Weapon Sales: The Dark Web hosts forums and marketplaces where firearms and other weapons are bought and sold.
- Stolen Data: Personal information, credit card details, and confidential corporate data are frequently traded.
- Counterfeit Currency and Documents: Users can obtain fake IDs, passports, and counterfeit money.
- Human Trafficking: The Dark Web provides channels for the sale and purchase of human beings and other forms of exploitation.
- Cybercrime Services: Services such as hacking tools, ransomware, and phishing kits are readily available.
Comparison of Legal vs. Illicit Uses:
| Aspect | Legal Uses | Illicit Uses |
|---|---|---|
| Purpose | Secure communication, privacy protection | Illegal trading, exploitation |
| Users | Journalists, activists, privacy advocates | Criminals, hackers |
| Transactions | Legitimate, encrypted | Anonymously funded, often with crypto |
| Regulation | Compliant with laws | Operate outside legal confines |
The Dark Web’s structure and operational mechanisms inadvertently facilitate a thriving underground economy, which poses significant challenges to law enforcement and cybersecurity. The illicit activities conducted on the Dark Web have a profound impact on society, from cybercrime and financial fraud to the spread of illegal goods, making it a contentious and heavily scrutinized aspect of the internet.
How the Deep Web and Dark Web Affect Everyday Life
The Deep Web and Dark Web have significant influences on various aspects of daily life, impacting how individuals and organizations handle security, privacy, and information access.
How the Deep Web Supports Secure Internet Activities
The Deep Web is integral to supporting secure internet activities that individuals and organizations rely on daily. Its hidden nature ensures that sensitive information is protected and accessible only to authorized users.
Supporting Secure Activities:
- Online Banking: Securely managing finances and conducting transactions without exposing personal financial data to potential attackers.
- Healthcare Services: Protecting patient records and medical histories, ensuring privacy and compliance with health regulations.
- Corporate Communications: Facilitating secure internal communications and data storage, preventing unauthorized access to proprietary information.
- Educational Databases: Providing students and researchers access to academic resources without compromising the integrity of the data.
Benefits of Deep Web for Secure Activities:
- Enhanced Security: Data stored on the Deep Web is shielded from public view, reducing the risk of unauthorized access and cyber threats.
- Privacy Protection: Personal and sensitive information remains private, safeguarding individuals from identity theft and privacy breaches.
- Compliance and Regulation: Ensures that organizations comply with data protection laws by securely managing and storing sensitive information.
- Reliable Access: Provides stable and controlled access to essential services, ensuring that important data is available when needed without being publicly accessible.
Examples of Secure Deep Web Activities:
- Bank Transactions: Encryption and secure logins protect financial information during online transactions.
- Corporate Data Management: Companies store critical business data in secure databases accessible only to authorized employees.
- Healthcare Record Keeping: Patient information is stored securely, ensuring confidentiality and compliance with health privacy laws.
The Deep Web’s role in supporting secure internet activities underscores its importance in today’s digital world, where security and privacy are paramount.
How the Dark Web Impacts Cybersecurity and Law Enforcement
The Dark Web significantly influences both cybersecurity practices and law enforcement strategies. Its role as a hub for illicit activities poses substantial challenges while also prompting advancements in cyber defense mechanisms.
Impact on Cybersecurity:
- Increased Threats: The Dark Web is a breeding ground for cyber threats, including malware distribution, ransomware, and identity theft.
- Data Breaches: Stolen data from breaches are often traded on the Dark Web, making victims more susceptible to further cyber attacks.
- Cybercrime Tools: Availability of hacking tools, phishing kits, and exploit programs facilitates the execution of cyberattacks.
Impact on Law Enforcement:
- Difficulty in Tracking Criminals: The anonymity provided by the Dark Web makes it challenging for law enforcement to identify and apprehend cybercriminals.
- Resource Allocation: Significant resources must be devoted to monitor, infiltrate, and investigate Dark Web activities.
- International Cooperation: Cybercrimes on the Dark Web often cross national borders, necessitating international collaboration among law enforcement agencies.
Key Challenges:
- Anonymity and Encryption: Anonymity networks like Tor hide users’ identities and locations, complicating tracking efforts.
- Volume of Activity: The vast amount of data and activities on the Dark Web make it difficult to sift through and identify threats.
- Technological Sophistication: Criminals use advanced encryption and anonymization tools to protect their operations, requiring equally sophisticated countermeasures from law enforcement.
Strategies to Combat Dark Web Threats:
- Digital Forensics: Employing advanced digital forensics to trace illicit activities back to their sources.
- Cyber Intelligence: Gathering and analyzing intelligence from the Dark Web to anticipate and prevent cyber threats.
- Collaborative Efforts: Working with cybersecurity firms and international bodies to share information and coordinate actions against cybercriminals.
Comparison of Traditional vs. Dark Web Cybersecurity:
| Aspect | Traditional Cybersecurity | Dark Web Impact |
|---|---|---|
| Threat Types | Viruses, ransomware, phishing | Advanced malware, complex exploits |
| Detection Methods | Antivirus, firewalls, IDS | Advanced digital forensics, AI-assisted detection |
| Response Strategies | Patch management, isolation | Infiltration, intelligence gathering |
The Dark Web’s impact on cybersecurity and law enforcement underscores the need for continuous innovation in cyber defense and collaborative international efforts to mitigate the risks associated with this hidden part of the internet.
How Businesses and Governments Monitor and Respond to Dark Web Threats
Businesses and governments employ a range of strategies to monitor and counteract threats emerging from the Dark Web. These proactive measures are essential for protecting sensitive information and maintaining national and corporate security.
Monitoring Strategies:
- Dark Web Crawlers: Automated tools that scan Dark Web forums, marketplaces, and other platforms to identify potential threats and illicit activities.
- Threat Intelligence Platforms: Aggregating and analyzing data from the Dark Web to identify emerging threats, vulnerabilities, and cybercriminal activities.
- Human Intelligence (HUMINT): Employing experts to interact and gather intelligence directly from Dark Web communities and marketplaces.
Response Measures:
- Incident Response Plans: Establishing protocols to respond swiftly to cyber incidents detected via Dark Web monitoring.
- Collaboration with Cybersecurity Firms: Partnering with specialized firms that offer expertise and tools for detecting and mitigating Dark Web threats.
- Legal Action: Coordinating with international law enforcement agencies to track and prosecute cybercriminals operating on the Dark Web.
Tools and Technologies:
- Dark Web Intelligence Tools: Platforms like Recorded Future and DarkOwl provide comprehensive monitoring and analysis of Dark Web activities.
- Encryption and Secure Communication: Ensuring that sensitive communications within government and corporate networks remain protected from Dark Web snoopers.
- User Behavior Analytics (UBA): Using machine learning and AI to detect unusual patterns that may indicate compromised systems or insider threats.
Collaborative Efforts:
- International Cooperation: Governments across the globe collaborate to share intelligence and coordinate efforts to dismantle Dark Web criminal networks.
- Public-Private Partnerships: Collaborating with private cybersecurity firms to leverage their expertise and technologies in combating Dark Web threats.
- Legislative Frameworks: Developing laws and regulations that empower law enforcement agencies to take effective action against Dark Web-based cybercrime.
Table of Common Monitoring and Response Tools:
| Tool/Strategy | Description | Purpose |
|---|---|---|
| Dark Web Crawlers | Automated scanners of Dark Web sites and forums | Detect illicit activities and threats |
| Threat Intelligence Platforms | Aggregates and analyzes Dark Web data | Identify and predict cyber threats |
| Human Intelligence (HUMINT) | Expert monitoring and interaction | Gather actionable intelligence |
| Incident Response Plans | Protocols for responding to cyber incidents | Mitigate and manage cyber threats |
| Public-Private Partnerships | Collaborations between government and firms | Enhance cybersecurity capabilities |
By employing these multifaceted approaches, businesses and governments can effectively monitor and respond to threats originating from the Dark Web, ensuring the protection of sensitive information and the overall security of digital infrastructures.

Frequently Asked Questions (FAQs)
1. What is the main difference between the Deep Web and Dark Web? The Deep Web refers to all parts of the internet not indexed by search engines, including legitimate databases and private networks. The Dark Web is a subset of the Deep Web that is intentionally hidden and requires special software like Tor to access, often associated with anonymity and both legitimate and illicit activities.
2. Can accessing the Dark Web be legal? Yes, accessing the Dark Web is legal in many countries. It can be used for legitimate purposes such as protecting privacy, secure communication for activists and journalists, and accessing information in restrictive environments. However, many activities on the Dark Web are illegal.
3. How safe is it to explore the Dark Web? Exploring the Dark Web can be risky due to the presence of malicious content, scams, and illegal activities. Users can inadvertently download malware or engage with criminal enterprises. It’s essential to use secure tools and exercise caution when navigating these hidden spaces.
4. What tools do you need to access the Dark Web? To access the Dark Web, you typically need specialized software like the Tor browser, which anonymizes your internet traffic. Additional security measures, such as VPNs and antivirus software, are recommended to enhance safety.
5. How do law enforcement agencies monitor the Dark Web? Law enforcement agencies use a combination of advanced technologies, cyber intelligence, digital forensics, and human intelligence to monitor and investigate activities on the Dark Web. Collaboration with cybersecurity firms and international bodies also plays a crucial role in combating cybercrime in these hidden networks.
Key Takeaways
The Deep Web comprises a vast majority of the internet, including secure databases and private networks.
The Dark Web is a hidden subset of the Deep Web that emphasizes anonymity and can support both legitimate and illicit activities.
Misconceptions often arise due to the similarity in terminology and the hidden nature of both the Deep Web and Dark Web.
Understanding the differences is crucial for cybersecurity, privacy protection, and responsible internet navigation.
Tor and other anonymity networks are essential tools for accessing the Dark Web, providing layers of privacy and security.
Both the Deep Web and Dark Web play significant roles in everyday life, influencing privacy, data security, and combating cyber threats.
Conclusion
The Deep Web and Dark Web represent integral and distinct parts of the internet, each playing crucial roles in our digital landscape. While the Deep Web primarily serves legitimate purposes by providing secure and private access to sensitive information, the Dark Web offers a space for anonymity that can be harnessed for both positive actions and illicit activities. Understanding the differences between these layers is essential for navigating the internet safely, protecting personal privacy, and mitigating the risks associated with cyber threats.
The Dark Web’s interplay with cybersecurity and law enforcement underscores the ongoing battle between protecting user privacy and combating cybercrime. As technology evolves, so too must the strategies employed to ensure that these hidden parts of the internet are used responsibly and securely. By fostering awareness and implementing robust security measures, individuals, organizations, and governments can leverage the benefits of the Deep Web while addressing the challenges posed by the Dark Web.
Ultimately, the existence of the Deep Web and Dark Web highlights the complex nature of the internet, emphasizing the need for continuous education, technological innovation, and collaborative efforts to maintain a balance between openness, privacy, and security in the digital age.

